Building a foundation for security in an IoT Implementation
Understand how you can set up a security strategy with the management of your tools.

Security is not a destination. It’s a constant for every technology roadmap.
An effective security strategy is delivered through ongoing management of tools and processes to help prevent system exposure to evolving threats. It’s a commitment that requires recurring investment in resources, time, education, and solutions.
Here are six critical steps you can take to building a foundation for security in your next IoT implementation:
1. Define – Spend the time necessary to develop a strong definition around what “secure” means for your technology implementation. There will be parts of your system architecture that are more sensitive to security threats than others, and a sound definition will allow you to concentrate your focus on the most important parts of your technology landscape. Get a baseline that includes everything from the system registry files, file system content and makeup, application listing, hardware interface inventory, machine health and network configuration. Once this baseline has been defined, you can constantly compare the current state of the solution to this baseline, identifying and alerting you to potential new vulnerabilities.
2. Isolate and Protect – Once you’ve identified those areas that require increased security focus, it’s important to then work to both isolate and limit access to those areas of the architecture. Examples of solutions that help drive this level of focus include network segmentation/isolation and data encryption.
3. Limit Points of Exposure – Limiting points of vulnerability and minimizing points of failure is essential in helping to prevent potential security threats. Examples include working to collapse data management, services, integrations, and applications into distinct and defendable components of the architecture, limiting redundancy and unintended points of access into your technology architecture.
4. Build a Defense Perimeter – After you have identified, isolated, centralized, and protected key areas of your solution, it’s time to surround them with constant monitoring and testing. It’s important to refine your security strategy through an effective and recurring use of standard security tools and methodologies. This includes your end-to-end security management system, including the people, process, and tools that are dedicated to protecting your solution. Maintaining a real-time view of the health of your solution through a centralized management system is equally important. If your systems are not connected to a central management platform you may already be exposed to risks and vulnerabilities and unaware of what may lie ahead. Not having a defense wall presents an opportunity cost that far outweighs the expense to put a centralized system in place.
5. Educate – Today’s security threats are already old news, with new vulnerabilities and risks emerging every day it’s important to stay educated on the evolving landscape of security solutions, best practices, compliance standards, and threats.
6. Repeat – Security is a recurring necessity and should be designed into any business, product, and technology roadmap. It is should not hold you back or prevent you from innovating. It’s simply a consideration that needs to be continuously respected and managed in order to deliver great products.
A decade ago, no one thought much about hackers infiltrating a network to gain access and control over an automobile, a healthcare device, a webcam or even a gas station pump. Nowadays, it’s happening with more and more regularity and there is a fine line between being one of those companies in the headlines and not.
The threats will continue to evolve but, with the foundation for security described above, your company can prepare to the best of its ability for whatever comes next.
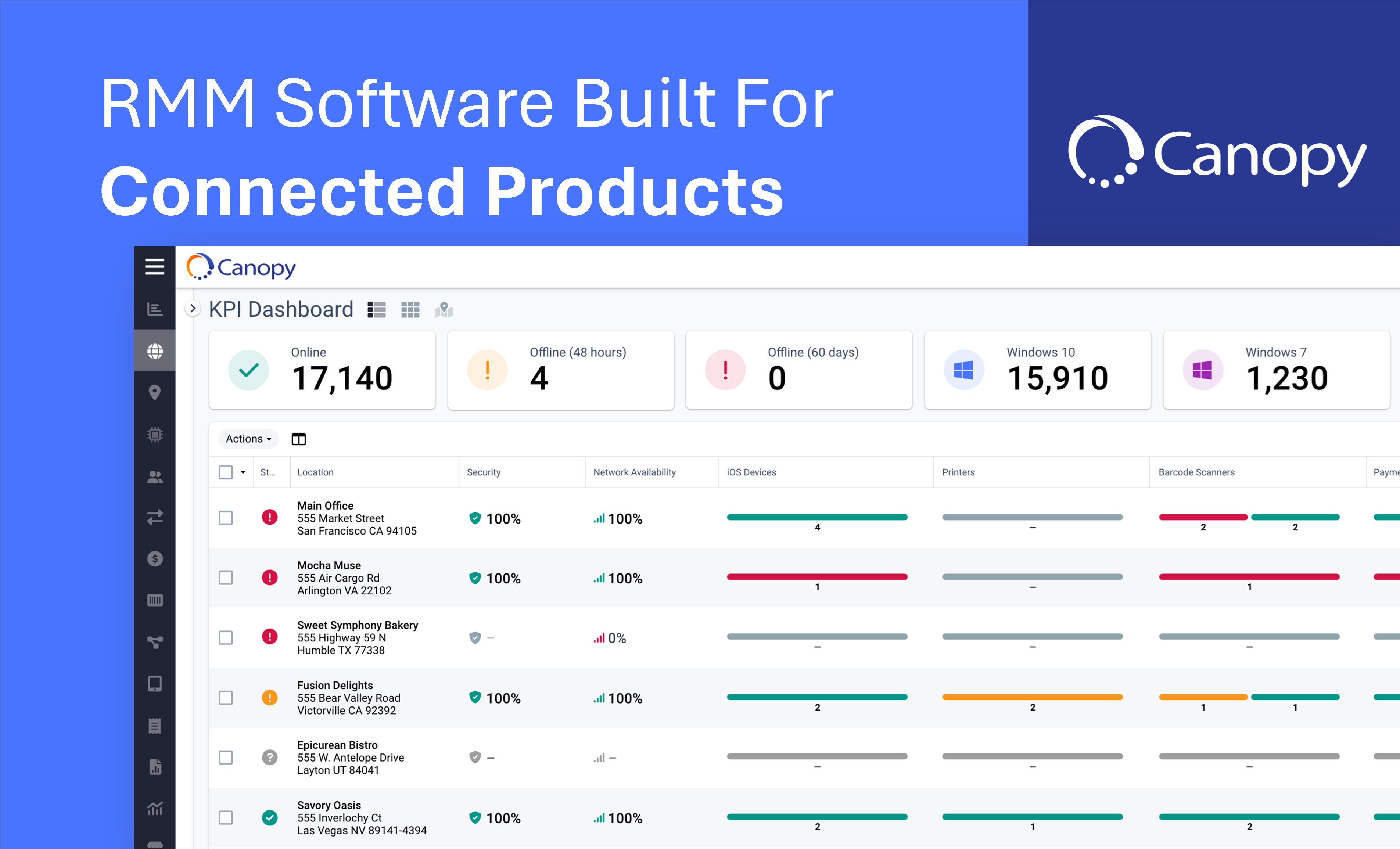
Don’t let threats prevent your company from innovating. Find out how an IoT platform like Canopy can provide help with security as well as other features such as real-time monitoring and incident management.